PREPARED BY:
Information Technology Department
DATE:
August 11, 2022
SUBJECT:
Cybersecurity
BACKGROUND/PURPOSE
The Windsor-Essex County Health Unit (WECHU) is committed to ensuring its information technology (IT) infrastructure and data housed therein, is secure. Our IT infrastructure plays an essential role in delivering services within the community of Windsor and Essex County. As such, it is crucial that the WECHU adopt measures around cybersecurity to “protect critical systems and sensitive information from digital attacks, whether those threats originate from inside or outside of the organization.” (IBM 2022) Recent examples of entities negatively impacted by cyber-related activities include:
- In June of 2022, the University of Windsor was impacted by a cybersecurity incident. The incident affected several platforms including the UWindsor website, Blackboard Learning Management System, UWinsit Student and campus Wifi. On a preliminary basis, it has been determined that personal data of associated users was secure and not subject to misuse.
- In June of 2022, Celero Solutions Inc., a third-party company that provides technology services to Northern Credit Union as well as other credit unions experienced a cybersecurity incident that compromised members’ private information.
DISCUSSION
The WECHU’s approach to cybersecurity focuses on four areas, its users, its IT infrastructure, the transfer of risk of financial loss and continuous improvement.
Users and IT infrastructure
The WECHU users, including staff and Board Members, represent the first layer in our approach to cybersecurity. Recognizing the importance of this layer, the WECHU has implemented a Cybersecurity Awareness Program and Training Policy (Policy). This Policy prescribes mandatory training at the beginning of employment with the WECHU and annually thereafter, or more frequently, if determined appropriate. It provides guidance regarding on-going communications with WECHU users regarding cyber-related activities. The Policy identifies the WECHU’s use of periodic phishing campaigns to test the competencies of the WECHU users, identifying those requiring additional training and education. Lastly, the Policy identifies a comprehensive reporting structure ensuring accountability and transparency surrounding the WECHU’s Cybersecurity Awareness Program.
The next layer in our approach to cybersecurity represents the WECHU’s Intrusion Detection System, more specifically, our Palo Alto Appliance. This allows the WECHU to stop known threats before they can connect to our IT infrastructure. The firewall also employs secure sockets layer (SSL) decryption, a method that allows the WECHU to see inside normally secure traffic.
The third layer in our approach to cybersecurity is our firewall. The firewall exposes a nominal portion of the WECHU network to the outside world. The WECHU only allow services such as inbound e-mail, and web-traffic to pass to the WECHU network. This traffic is untrusted and moved into a zone of control. The zone of control allows us to read the packets of data to ensure it is safe for forwarding on through the next layer. The WECHU maintains several zones to prevent communication between services and computers that are not required. For example, once the Barracuda E-mail Security Gateway processes our e-mail traffic, it is the only device that can forward e-mail traffic directly to our firewall, which in turn gets sent to our e-mail servers. These basic zones of control ensure that a compromised node (server or workstation) is limited in the extent of the WECHU infrastructure that it interacts with.
The Barracuda E-mail Security Gateway, looks at all e-mail before delivery to our mail servers. This allows the IT Department to inspect, remove or quarantine e-mails before reaching the network. Additionally, the gateway has Advanced Threat Protection (ATP) which automatically scans e-mail attachments in real-time; suspicious attachments are detonated in a sandbox environment to observe behaviour. In addition to blocking the attachment, the results are integrated into the Barracuda Real Time Intelligence System providing protection for all other customers. (Barracuda Networks 2022)
The fourth layer in our approach to cybersecurity is the Antimalware. Antimalware engines at both the firewall and desktop levels monitor the behavior of applications using a decision model to determine if the applications are behaving as anticipated. If they are not, the system quarantines the process, notifying the IT Department immediately of the potential threat.
The fifth layer in our approach to cybersecurity is the WECHU’s antivirus application. When retrieving files and processes, the computer accesses memory, which are reviewed and sandboxed or tested, until proven safe. This process can quickly identify files as they move between workstations and the internet or vice versa.
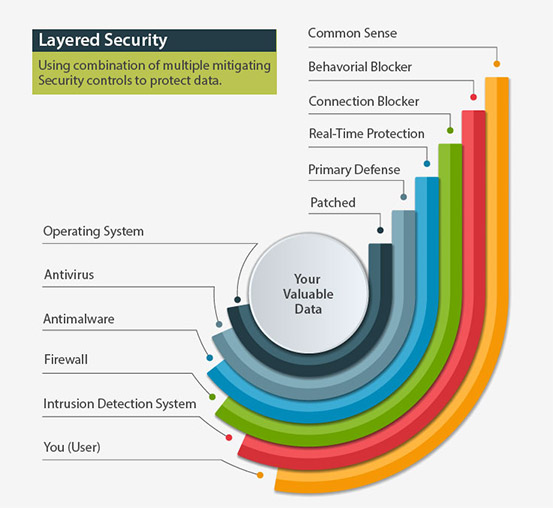
The final layer of the WECHU’s approach to cybersecurity are the operating systems. The WECHU IT Department monitors operating systems including Windows, Linux and vendor proprietary systems. Daily, the IT Department reads bulletins, release notes and threat assessments and determines what actions are required to mitigate the risk of a cyber-threat. By maintaining current patches, and eliminating legacy systems or protocols, the IT Department is able to provide a secure environment for WECHU staff to carry out their responsibilities.
Transfer of Risk of Financial Loss
To address the transfer of risk of financial loss resulting from a cyber-related incident, the WECHU has engaged third-party insurer. Specific coverage provided under the policy include:
- Breach response services due to an actual or reasonable suspected Data Breach or Security Breach including legal, forensic and public relations/crisis management support.
- First party loss coverage including business interruption, dependent business loss, reputational loss, cyber extortion loss, hardware replacement and data recovery.
- Liability coverage including data and network liability, regulatory defence and penalties, payment care liabilities and costs and media liability.
- eCrime coverage including fraudulent instruction, funds transfer fraud, telephone fraud, impersonation fraud loss.
- Criminal reward coverage.
The insurance policy is renewed annually through a detailed application process. Policy limits are subject to change depending upon contractual requirements the WECHU is subject to (i.e. Data Sharing Agreements) as well as industry-related changes (i.e. changes in insurable limits available through third party providers).
Continuous Improvement
The topic of cybersecurity is continuously evolving. As such, the WECHU must actively improve its approaches to cybersecurity. Currently, the WECHU is undertaking a procurement process to engage a third-party consultant to perform penetration testing. The purpose of penetration testing it to simulate a cyber attack on the WECHU’s IT infrastructure identifying and exploiting vulnerabilities. Once identified, the WECHU can remediate vulnerabilities reducing the risk that its IT infrastructure will be negatively impacted by cyber-related activities or events.

